What is Tor and how does it work?
Exploring Tor - because VPNs aren't the only way to stay anonymous online

If you're looking to keep your online activities to yourself then Tor (The Onion Router) is a great addition to your privacy toolkit.
The Tor Project offers a custom Tor Browser, with clever open-source technology using some very smart tricks to protect your privacy online.
It accesses both regular websites and the dark web, the hidden area of the internet which you won't find indexed on Google.
And, as open-source software, it's also free, with no registration required, no data limits, no ads and no constant demands to upgrade to a paid product. However, the Tor Project accepts donations.
Is Tor the perfect web anonymity and privacy tool? Not quite, but it can work very well in some situations. Let’s see how Tor works, when to use it, and how you can combine it with the best VPNs to get the best possible protection.
How does Tor work?
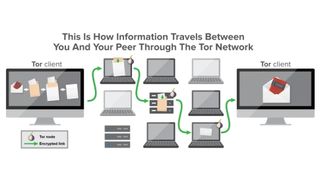
Tor is an open-source package based around a principle called Onion Routing.
This involves encrypting your data multiple times, then passing it through a network of volunteer-run servers (or 'relays') from around the world.
Are you a pro? Subscribe to our newsletter
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!
Your own Tor ‘client’ software kicks things off by selecting a list of ‘nodes’ through which your data will pass. This is sometimes known as a ‘circuit’. This information is downloaded from a main ‘directory’ node and made available only to your device - no one else can tell which specific nodes you’re using from analysing your connection data.
Your device then uses asymmetric or public key encryption to send an encrypted message to the first (or 'guard') relay. This first relay receives your data and peels off the first layer of encryption, like the layer of an onion. Now you know why Tor stands for 'The Onion Router', taking its name from this layering idea.
The guard relay knows your IP address but has no other clues to your identity. It can't see which site you're trying to access, either, so there's no way to log what you're doing beyond the fact that a connection has been made to the Tor network from your IP address. Using encryption your device and the first relay will also establish a shared ‘session key’ to further encrypt your data.
The only other information it has is the address of the next relay. Your device can then pass encrypted information to the first node, which it can’t decrypt - the data is passed onto the second node.
The second node and indeed any subsequent relays don't have your IP address or know which site you're trying to visit. All they do is remove a layer of encryption and pass the data to the next relay. They don’t even know if the node that just connected to them is the very first node in the circuit or the 100th in a series.
When your data reaches the last relay, also called the exit node, it removes the final layer of encryption and routes your web request to its real destination.
Your target website sees the IP address of the Tor exit node rather than yours, so has even less idea of who you are. It passes its response back to the exit node, which routes it through the Tor network and back to you by simply reversing the process : data is encrypted and passed along the same circuit but at each stage it can only remove the previous layer of encryption, meaning data is only readable when it arrives on your device.
A word on hidden services
The above example assumes that you’re accessing the regular internet via Tor. Tor users can also access specialized ‘hidden services’ which exist only in the dark net. These are identified by the domain suffix .onion and can only be accessed via the Tor browser or software running the Tor client.
Using hidden services benefits both to people accessing sites on the Tor network and people who want to run them. In the first place, the Onion protocol doesn’t rely on IP addresses or even DNS. Each .onion address is unique, so provided you’re sure the address is correct you can be certain you’re visiting the right site.
This is part of the reason that hidden service addresses look so “weird and random”, as the Tor Project website, puts it. Expect to see addresses like. vww6ybal4bd7szmgncyruucpgfkqahzddi37ktceo3ah7ngmcopnpyyd.onion
The address contains the ‘public key’ of the website so it’s possible for the network to verify that it’s genuine. Of course anyone can set up a site pretending to be someone else, so it’s important you get this address from a reliable source.
Keeping your traffic within the Tor network will speed things up, as the Tor network establishes ‘long term’ circuits to allow for easier connections. Using a hidden service also means you get around the problem of exit relays run by bad actors or ‘poisoned nodes’ as they’re known in the trade. As you’re not accessing the regular Internet, you don’t need them.
This type of anonymity works both ways. There’s no way to tell the identity or IP address behind a .onion domain just by connecting to it. This means .onion sites are sometimes used to host illegal content. Be warned, stay vigilant.
.onion sites aren't only used by people looking to hide something, though. They're also a way to bypass censorship, perhaps to get around country-level website blocks. Facebook, the BBC, and DuckDuckGo all have .onion sites that can only be opened in the Tor Browser.
Certain websites are still using the shorter ‘v2’ addresses, which are being phased out by the Tor Project due to a vulnerability which under some circumstances could allow users to be identified. Officially the v2 addresses are no longer supported, so make sure only to use the v3 addresses instead.
It's not always easy to find the correct address for .onion sites, but there are plenty of resources that can help. The Hidden WiKi is a huge .onion site directory. DuckDuckGo indexes .onion sites, and the sub-Reddit /r/onions has plenty of chat and recommendations about the latest .onion discoveries. Ideally, check with someone at the organization whose hidden service you want to visit that the .onion address is correct.
Is Tor a VPN?
There are major differences when it comes to comparing Tor vs VPNs. Tor uses the same core principle as a VPN service. It hides your IP address from websites by routing your traffic through another server. But how the process works is not the same.
For example, while VPNs typically use a single VPN server, Tor routes your data through at least three.
VPNs usually employ protocols with a single layer of encryption which protects you from end-to-end; Tor uses multiple layers, but these are peeled off as you travel from server to server.
VPNs require you to log into a server, which then sees every website you visit (and could log that data, theoretically, especially when using some free VPNs). Of course many VPN providers claim to operate a “no logs” policy so that they can’t read your personal data but not all of them submit to regular VPN audits by a trusted third party to make sure this is the case.
Tor separates the knowledge of who you are (your incoming IP address) and the website you're visiting, making it much more difficult to record your activities. A bad actor operating a ‘poisoned’ exit node could in theory harvest unencrypted information you entered into websites on the regular internet.
This is why you should either make sure you only access ‘clearnet’ websites via Tor that only allow connections via SSL and TLS as your data will then be encrypted. Better yet, use only Tor hidden services so your data doesn’t have to be decrypted in transit.
Perhaps the biggest difference is in use. Rare is the organization favoring Tor, while you'll find plenty of business VPNs in the office.
VPNs are also very popular for watching geo-specific or region-locked content, leading to the rise in Netflix VPNs, streaming VPNs, and even VPNs for torrenting,
Learn more about VPNs in our guide Everything you need to know about Virtual Private Networks.
How do I use Tor?
Despite Tor's powerful tech and many privacy-protecting features, it's very easy to use.
Visit the official Tor website and download the right version of Tor for your platform. The site offers downloads of the Tor Browser for Windows, Mac, Linux and Android. There’s no official iOS download but the Tor Project recommend using the Onion Browser, which is open source and apparently run by someone close to the project. They caution though that as Apple requires using the browser engine ‘WebKit’ which can undermine your privacy.
Running the installer sets your device up with Tor Browser, a special version of Firefox. This includes the extra software necessary to make Tor work, and also bundles the excellent NoScript and HTTPS Everywhere extensions for even more protection.
Launch Tor Browser and it asks if you'd like to connect to Tor. Click Connect, Tor Browser connects to a Tor guard relay, and that's it, you can get on with running searches, browsing to websites and generally using the web as normal. The only difference is your traffic is now routed via the Tor network, rather than your regular connection.
Remember that unlike a VPN, the Tor Browser only will protect its own traffic. If you want to use another application with Tor, you’ll need to download the Tor client and manually configure each app to access Tor via SOCKS5 Proxy.
Is Tor illegal?
The dark web is often linked to sites selling guns, drugs, stolen data and all kinds of horrifying content. Although there's some truth in that, it's only a tiny part of the story.
Tor has a similar legal status to VPNs across much of the world. The technology won't cause you any legal problems in most countries - as long as you don't use it to order illicit items from deep web sites, anyway.
Countries which ban VPNs, like China, Belarus and the UAE, also disapprove of Tor. That doesn't mean you'll be arrested for downloading it - China is more interested in blocking the technology, so it just won't work - but it does mean you should be more careful. If you're using a VPN for China or elsewhere anyway, combining it with Tor might prevent the authorities seeing what you're doing.
What are the disadvantages of Tor?
Encrypting your traffic and routing it through multiple servers does a lot to protect your privacy, but there's a price to pay. It really, really, really slows you down.
How slow? We ran a speed test on a mobile device connected via Wi-Fi. This managed downloads of 50Mbps using our regular connection, and 2Mbps with Tor. Compared to the fastest VPNs, this is very slow.
There's another potential problem, too. Many hackers abuse Tor as a way to protect their identity when they launch attacks. Platforms understand this very well, and many display warnings or block access entirely if they detect you're using Tor.
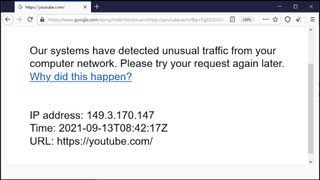
PayPal gave us a couple of extra security checks and still blocked our login attempts. Amazon let us in, but only after we'd approved a notification sent to our mobile. And Google blocked us out of YouTube entirely because 'our systems have detected unusual traffic from your computer network', it complained. Tor probably isn't going to be a good choice for your regular browsing.
Part of the reason for this is that Tor chooses exit nodes at random, so you can be seen to be trying to log in from multiple locations. It is possible to configure the Tor Browser to use “strict nodes” from only one country to make this more manageable but if there aren’t any exit relays available in your country of choice when you go online, you’ll have to wait.
Is Tor secure?
Tor's big anonymity advantage is that it's decentralized. The Tor network isn't run by a single company who gets to see every connection and data path: relays are run by thousands of volunteers from around the world. There's no one point anyone can use to watch your logins, record your traffic or otherwise monitor what you're doing online.
Your own network can see you're accessing Tor, though, which might be a problem in a country which doesn't like web privacy. And although the first Tor relay doesn't need any logon credentials, it has a little knowledge about you in the shape of your IP address.
If you live in a country which restricts or bans usage of Tor, you can indicate this when launching the browser. Tor will connect you to a virtual ‘bridge’ relay. Like ordinary relays, these are run by volunteers but are not listed publicly, so are harder to detect. By connecting to the Tor network via a bridge your ISP and anyone with access to their records will find it extremely difficult to detect you’re using the Tor network, making it harder to block.
There is a potential vulnerability in the Tor exit node, too, the server which both removes the final layer of encryption and gets to see the URL you're trying to visit. If you're using an unencrypted HTTP, rather than an HTTPS connection, the node may be able to log sensitive information about your activities. This is why the Tor Browser comes with the HTTPS Everywhere add-on which forces the software to connect securely where available.
Exit nodes can still sometimes use an exploit called SSL stripping to access unencrypted HTTP communications on what you think is an encrypted site though. In August 2020, security researcher nusenu unveiled research suggesting up to 23% of all Tor exit nodes were engaged in a malicious campaign targeting accesses to cryptocurrency sites, altering traffic and redirecting transactions into their own virtual wallets.
Again, these kinds of issues won’t occur if you simply keep your traffic in the Tor network by only visiting .onion addresses, as your data is encrypted at all times anyway.
What’s the safest way to use Tor?
Tor goes a long way to preserving your web privacy, but it has some issues. If you're looking for maximum protection, the best approach is to combine Tor with a VPN.
The simplest route is to connect to your VPN, then Tor (a technique called 'Onion over VPN'.) Now your home network only sees your VPN IP, so it doesn't know you're accessing Tor. The first Tor relay only sees your VPN IP address, giving it no information on who you are. And your VPN can't see which sites you're browsing as they're handled by Tor, so even if a server is breached by hackers, there's no way to access your browsing history.
Tor over VPN can't always protect you from malicious exit nodes, which is why some users prefer connecting to Tor first, then the VPN ('VPN over Onion'.) But that allows the VPN to see your traffic again, giving you little privacy benefit overall.
You can use Tor with most VPNs, but some have better support than others.
ExpressVPN has its own older v2 .onion site for instance, making it easier to access the service in countries where it's blocked but we were unable to find a newer v3 .onion address for them. (They do have a great Tor guide, too though.)
NordVPN has built-in Onion over VPN support, so you don't even need the Tor browser. Just choose Onion Over VPN in the NordVPN app and it connects you to the Tor network: web privacy doesn't get much easier than that, plus it’s an easy way to ensure that all your apps can use the Tor network, not just your web browser.
Remember that you might still be identified through your online activity in other ways such as browser fingerprinting.
If someone gains access to your device, they also may be able to examine your apps and view your web history. The Tor Browser is automatically configured not to save history of websites you visit, though of course you can bookmark .onion addresses in the same way as regular pages.
- Best cheap VPN: Just because it's cheap, doesn't mean it's bad

Mike is a lead security reviewer at Future, where he stress-tests VPNs, antivirus and more to find out which services are sure to keep you safe, and which are best avoided. Mike began his career as a lead software developer in the engineering world, where his creations were used by big-name companies from Rolls Royce to British Nuclear Fuels and British Aerospace. The early PC viruses caught Mike's attention, and he developed an interest in analyzing malware, and learning the low-level technical details of how Windows and network security work under the hood.
Most Popular


